Auto Bcc Keygen Idm
Download IDM Patch 2018 เลือกโหลดได้เหมือนกันทั้ง 2 ลิงค์ [Review] [Review] วิธีใช้งาน IDM Patch 2017 1. ติดตั้งโปรแกรม IDM ตามปกติ (Install IDM) - ใครมีโปรแกรม IDM ในเครื่องอยู่แล้วที่หมดอายุ เด้งซีเรียลนัมเบอร์ปลอม (Fake Serial Number) ไม่อยากติดตั้งใหม่ก็ข้ามไปขั้นตอนต่อไปได้เลย - ใครต้องการติดตั้ง IDM เวอร์ชั่นล่าสุด สามารถดาวน์โหลดได้ในเว็บ 2.
ปิดโปรแกรม IDM ทั้งที่อยู่หน้าจอและที่อยู่ตรง Taskbar มุมล่างขวาหน้าจอคอมพิวเตอร์ของคุณออก 3. ปิดโปรแกรมแอนตี้ไวรัสก่อนเพราะการทำงานของ IDM Patch โปรแกรมแอนตี้ไวรัสอาจมองเป็นภัยคุกคามแต่ความจริงปลอดภัยไม่มีไวรัสแต่อย่างใด 4. คัดลอกไฟล์ Patch ไปวางในโฟลเดอร์ที่ติดตั้งโปรแกรม - หากเป็น Windows 32 bit ก็จะอยู่ใน C: Program Files Internet Download Manager - แต่ถ้าเป็น Windows 64 bit จะอยู่ใน C: Program Files (x86) Internet Download Manager 5. Click Patch 6.

ในช่อง Enter first name: พิมพ์ idm 7. ในช่อง Enter last name or nothing: พิมพ์ download ถ้าใครไม่อยากใช้ IDM Patch หรือมีปัญหาใช้งานไม่ได้ ให้โหลด IDM ตัวล่าสุดตรงหัวข้อโพสต์แนะนำ ไปใช้นะ ตัวนั้นไม่ต้องใช้ Patch 😃😃😃😃 โหลดได้ ไม่ได้ ใช้ดี ไม่ดี Comment กันด้วยนะ ทดลองใช้งานแล้วใช้งานได้ 100%. ติดตั้งโปรแกรม IDM - ใครมีโปรแกรม IDM ในเครื่องอยู่แล้วที่หมดอายุ เด้งซีเรียลนัมเบอร์ปลอม (Fake Serial Number) ไม่อยากติดตั้งใหม่ก็ข้ามไปขั้นตอนต่อไปได้เลย - ใครต้องการติดตั้ง IDM เวอร์ชั่นล่าสุด สามารถดาวน์โหลดได้ด้านล่าง 2. ปิดโปรแกรม IDM ทั้งที่อยู่หน้าจอและที่อยู่ตรง Taskbar มุมล่างขวาหน้าจอคอมพิวเตอร์ของคุณออก 3. ปิดโปรแกรมแอนตี้ไวรัสก่อนเพราะการทำงานของ IDM Patch โปรแกรมแอนตี้ไวรัสอาจมองเป็นภัยคุกคามแต่ความจริงปลอดภัยไม่มีไวรัสแต่อย่างใด 4. คัดลอกไฟล์ Patch ไปวางใน - ถ้าเป็น Windows 32 bit จะอยู่ใน C: Program Files Internet Download Manager - แต่ถ้าเป็น Windows 64 bit จะอยู่ใน C: Program Files (x86) Internet Download Manager 5.
รันไฟล์ Patch 6. ในช่อง Enter first name: พิมพ์ idmdownload 7. ในช่อง Enter last name or nothing: พิมพ์ info 8. กด Register รอจนกว่าจะขึ้น Register succerful!, แล้วกด OK. กด Patch รอจนกว่าจะขึ้น File update succerful! Bugs removed:-), แล้วกด OK.
ForgeRock publishes comprehensive documentation online: • The ForgeRock offers a large and increasing number of up-to-date, practical articles that help you deploy and manage ForgeRock software. While many articles are visible to community members, ForgeRock customers have access to much more, including advanced information for customers using ForgeRock software in a mission-critical capacity. • ForgeRock product documentation, such as this document, aims to be technically accurate and complete with respect to the software documented. It is visible to everyone and covers all product features and examples of how to use them.
OpenIDM infrastructure modules provide the underlying features needed for core services: BPMN 2.0 Workflow Engine OpenIDM provides an embedded workflow and business process engine based on Activiti and the Business Process Model and Notation (BPMN) 2.0 standard. For more information, see. Task Scanner OpenIDM provides a task-scanning mechanism that performs a batch scan for a specified property in OpenIDM data, on a scheduled interval. The task scanner then executes a task when the value of that property matches a specified value. For more information, see.
Destination an Autocom Delphi 2013 2 Keygen Idm amid the SUV pods and uninteresting sedans of today’s. It is an auto that seems to own been pushed straight.
Scheduler The scheduler provides a cron-like scheduling component implemented using the. Use the scheduler, for example, to enable regular synchronizations and reconciliations. For more information, see. Script Engine The script engine is a pluggable module that provides the triggers and plugin points for OpenIDM. OpenIDM currently supports JavaScript and Groovy. Policy Service OpenIDM provides an extensible policy service that applies validation requirements to objects and properties, when they are created or updated.
For more information, see. Audit Logging Auditing logs all relevant system activity to the configured log stores. This includes the data from reconciliation as a basis for reporting, as well as detailed activity logs to capture operations on the internal (managed) and external (system) objects.
For more information, see. Repository The repository provides a common abstraction for a pluggable persistence layer.
OpenIDM 4.5 supports reconciliation and synchronization with several major external repositories in production, including relational databases, LDAP servers, and even flat CSV and XML files. The repository API uses a JSON-based object model with RESTful principles consistent with the other OpenIDM services. To facilitate testing, OpenIDM includes an embedded instance of OrientDB, a NoSQL database. You can then incorporate a supported internal repository, as described in in the Installation Guide. The core services are the heart of the OpenIDM resource-oriented unified object model and architecture: Object Model Artifacts handled by OpenIDM are Java object representations of the JavaScript object model as defined by JSON.
The object model supports interoperability and potential integration with many applications, services, and programming languages. OpenIDM can serialize and deserialize these structures to and from JSON as required. OpenIDM also exposes a set of triggers and functions that system administrators can define, in either JavaScript or Groovy, which can natively read and modify these JSON-based object model structures. Managed Objects A managed object is an object that represents the identity-related data managed by OpenIDM. Managed objects are configurable, JSON-based data structures that OpenIDM stores in its pluggable repository. The default managed object configuration includes users and roles, but you can define any kind of managed object, for example, groups or devices.
You can access managed objects over the REST interface with a query similar to the following: $ curl --header 'X-OpenIDM-Username: openidm-admin' --header 'X-OpenIDM-Password: openidm-admin' --request GET 'System Objects System objects are pluggable representations of objects on external systems. For example, a user entry that is stored in an external LDAP directory is represented as a system object in OpenIDM. System objects follow the same RESTful resource-based design principles as managed objects.
They can be accessed over the REST interface with a query similar to the following: $ curl --header 'X-OpenIDM-Username: openidm-admin' --header 'X-OpenIDM-Password: openidm-admin' --request GET 'There is a default implementation for the OpenICF framework, that allows any connector object to be represented as a system object. Mappings Mappings define policies between source and target objects and their attributes during synchronization and reconciliation. Mappings can also define triggers for validation, customization, filtering, and transformation of source and target objects. For more information, see. Synchronization and Reconciliation Reconciliation enables on-demand and scheduled resource comparisons between the OpenIDM managed object repository and source or target systems. Comparisons can result in different actions, depending on the mappings defined between the systems.
Synchronization enables creating, updating, and deleting resources from a source to a target system, either on demand or according to a schedule. For more information, see.
1.4. Secure Commons REST Commands Representational State Transfer (REST) is a software architecture style for exposing resources, using the technologies and protocols of the World Wide Web. For more information on the ForgeRock REST API, see. REST interfaces are commonly tested with a curl command. Many of these commands are used in this document.
They work with the standard ports associated with Java EE communications, 8080 and 8443. To run curl over the secure port, 8443, you must include either the --insecure option, or follow the instructions shown in. You can use those instructions with the self-signed certificate generated when OpenIDM starts, or with a *.crt file provided by a certificate authority.
In many examples in this guide, curl commands to the secure port are shown with a --cacert self-signed.crt option. Instructions for creating that self-signed.crt file are shown in. You can also start OpenIDM as a background process on UNIX and Linux. Follow these steps before starting OpenIDM for the first time. • If you have already started OpenIDM, shut down OpenIDM and remove the Felix cache files under openidm/felix-cache/: ->shutdown. $ rm -rf felix-cache/* • Start OpenIDM in the background. The nohup survives a logout and the 2>&1& redirects standard output and standard error to the noted console.out file: $ nohup./startup.sh >logs/console.out 2>&1& [1] 2343 To stop OpenIDM running as a background process, use the shutdown.sh script: $./shutdown.sh./shutdown.sh Stopping OpenIDM (2343) Incidentally, the process identifier (PID) shown during startup should match the PID shown during shutdown.
The startup.sh script enables you to specify the following elements of a running OpenIDM instance: • --project-location or -p /path/to/project/directory The project location specifies the directory with OpenIDM configuration and script files. All configuration objects and any artifacts that are not in the bundled defaults (such as custom scripts) must be included in the project location. These objects include all files otherwise included in the openidm/conf and openidm/script directories.
For example, the following command starts OpenIDM with the configuration of Sample 1, with a project location of /path/to/openidm/samples/sample1: $./startup.sh -p /path/to/openidm/samples/sample1 If you do not provide an absolute path, the project location path is relative to the system property, user.dir. OpenIDM then sets launcher.project.location to that relative directory path. Alternatively, if you start OpenIDM without the -p option, OpenIDM sets launcher.project.location to /path/to/openidm/conf. When we refer to 'your project' in ForgeRock's OpenIDM documentation, we're referring to the value of launcher.project.location.
• --working-location or -w /path/to/working/directory The working location specifies the directory to which OpenIDM writes its database cache, audit logs, and felix cache. The working location includes everything that is in the default db/ and audit/, and felix-cache/ subdirectories. The following command specifies that OpenIDM writes its database cache and audit data to /Users/admin/openidm/storage: $./startup.sh -w /Users/admin/openidm/storage If you do not provide an absolute path, the path is relative to the system property, user.dir.
If you do not specify a working location, OpenIDM writes this data to the openidm/db, openidm/felix-cache and openidm/audit directories. Note that this property does not affect the location of the OpenIDM system logs. To change the location of the OpenIDM logs, edit the conf/logging.properties file.
You can also change the location of the Felix cache, by editing the conf/config.properties file, or by starting OpenIDM with the -s option, described later in this section. • --config or -c /path/to/config/file A customizable startup configuration file (named launcher.json) enables you to specify how the OSGi Framework is started. Unless you are working with a highly customized deployment, you should not modify the default framework configuration. This option is therefore described in more detail in. • --storage or -s /path/to/storage/directory Specifies the OSGi storage location of the cached configuration files. You can use this option to redirect output if you are installing OpenIDM on a read-only filesystem volume.
For more information, see in the Installation Guide. This option is also useful when you are testing different configurations. Sometimes when you start OpenIDM with two different sample configurations, one after the other, the cached configurations are merged and cause problems.
Specifying a storage location creates a separate felix-cache directory in that location, and the cached configuration files remain completely separate. By default, properties files are loaded in the following order, and property values are resolved in the reverse order. 2.3. Monitoring the Basic Health of an OpenIDM System Due to the highly modular, configurable nature of OpenIDM, it is often difficult to assess whether a system has started up successfully, or whether the system is ready and stable after dynamic configuration changes have been made. OpenIDM includes a health check service, with options to monitor the status of internal resources.
To monitor the status of external resources such as LDAP servers and external databases, use the commands described in. • infocontext specifies the relative name of the info endpoint under the info context.
The information can be accessed over REST at this endpoint, for example, setting infocontext to mycontext/myendpoint would make the information accessible over REST at • type specifies the type of the information source. JavaScript ( 'type': 'text/javascript') and Groovy ( 'type': 'groovy') are supported. • file specifies the path to the JavaScript or Groovy file, if you do not provide a 'source' parameter.
• source specifies the actual JavaScript or Groovy script, if you have not provided a 'file' parameter. Additional properties can be passed to the script as depicted in this configuration file ( openidm/samples/infoservice/conf/info- name.json).
Script files in openidm/samples/infoservice/script/info/ have access to the following objects. 2.3.5. Verifying the State of Health Check Service Modules The configurable OpenIDM health check service can verify the status of required modules and services for an operational system. During system startup, OpenIDM checks that these modules and services are available and reports on whether any requirements for an operational system have not been met. If dynamic configuration changes are made, OpenIDM rechecks that the required modules and services are functioning, to allow ongoing monitoring of system operation.
OpenIDM checks all required modules. Examples of those modules are shown here: 'org.forgerock.openicf.framework.connector-framework' 'org.forgerock.openicf.framework.connector-framework-internal' 'org.forgerock.openicf.framework.connector-framework-osgi' 'org.forgerock.openidm.audit' 'org.forgerock.openidm.core' 'org.forgerock.openidm.enhanced-config' 'org.forgerock.openidm.external-email'.
OpenIDM checks all required services. Examples of those services are shown here: 'org.forgerock.openidm.config' 'org.forgerock.openidm.provisioner' 'org.forgerock.openidm.provisioner.openicf.connectorinfoprovider' 'org.forgerock.openidm.external.rest' 'org.forgerock.openidm.audit' 'org.forgerock.openidm.policy' 'org.forgerock.openidm.managed' 'org.forgerock.openidm.script' 'org.forgerock.openidm.crypto' 'org.forgerock.openidm.recon' 'org.forgerock.openidm.info' 'org.forgerock.openidm.router' 'org.forgerock.openidm.scheduler' 'org.forgerock.openidm.scope' 'org.forgerock.openidm.taskscanner'. You can replace the list of required modules and services, or add to it, by adding the following lines to your project's conf/boot/boot.properties file.
Bundles and services are specified as a list of symbolic names, separated by commas: • openidm.healthservice.reqbundles - overrides the default required bundles. • openidm.healthservice.reqservices - overrides the default required services. • openidm.healthservice.additionalreqbundles - specifies required bundles (in addition to the default list).
• openidm.healthservice.additionalreqservices - specifies required services (in addition to the default list). By default, OpenIDM gives the system 15 seconds to start up all the required bundles and services, before the system readiness is assessed. Note that this is not the total start time, but the time required to complete the service startup after the framework has started. You can change this default by setting the value of the servicestartmax property (in milliseconds) in your project's conf/boot/boot.properties file. This example sets the startup time to five seconds: openidm.healthservice.servicestartmax=5000. • Start OpenIDM with the jpda option: $ cd /path/to/openidm $./startup.sh jpda Executing./startup.sh.
Using OPENIDM_HOME: /path/to/openidm Using OPENIDM_OPTS: -Xmx1024m -Xms1024m -Denvironment=PROD -Djava.compiler=NONE -Xnoagent -Xdebug -Xrunjdwp:transport=dt_socket,address=5005,server=y,suspend=n Using LOGGING_CONFIG: -Djava.util.logging.config.file=/path/to/openidm/conf/logging.properties Listening for transport dt_socket at address: 5005 Using boot properties at /path/to/openidm/conf/boot/boot.properties ->OpenIDM version '4.5.1-6' (revision: xxxx) OpenIDM ready The relevant JPDA options are outlined in the startup script ( startup.sh). • In your IDE, attach a Java debugger to the JVM via socket, on port 5005. To run OpenIDM as a service, take the following steps: • If you have not yet installed OpenIDM, follow the procedure described in in the Installation Guide. • Run the RC script: $ cd /path/to/openidm/bin $./create-openidm-rc.sh • As a user with administrative privileges, copy the openidm script to the /etc/init.d directory: $ sudo cp openidm /etc/init.d/ • If you run Linux with SELinux enabled, change the file context of the newly copied script with the following command: $ sudo restorecon /etc/init.d/openidm You can verify the change to SELinux contexts with the ls -Z /etc/init.d command.
For consistency, change the user context to match other scripts in the same directory with the sudo chcon -u system_u /etc/init.d/openidm command. • Run the appropriate commands to add OpenIDM to the list of RC services: • On Red Hat-based systems, run the following commands: $ sudo chkconfig --add openidm $ sudo chkconfig openidm on • On Debian/Ubuntu systems, run the following command: $ sudo update-rc. The Poor Man Said My Horse. d openidm defaults Adding system startup for /etc/init.d/openidm. /etc/rc0.d/K20openidm ->./init.d/openidm /etc/rc1.d/K20openidm ->./init.d/openidm /etc/rc6.d/K20openidm ->./init.d/openidm /etc/rc2.d/S20openidm ->./init.d/openidm /etc/rc3.d/S20openidm ->./init.d/openidm /etc/rc4.d/S20openidm ->./init.d/openidm /etc/rc5.d/S20openidm ->./init.d/openidm Note the output, as Debian/Ubuntu adds start and kill scripts to appropriate runlevels. When you run the command, you may get the following warning message: update-rc.d: warning: /etc/init.d/openidm missing LSB information. You can safely ignore that message. • As an administrative user, start the OpenIDM service: $ sudo /etc/init.d/openidm start Alternatively, reboot the system to start the OpenIDM service automatically. • (Optional) The following commands stops and restarts the service: $ sudo /etc/init.d/openidm stop $ sudo /etc/init.d/openidm restart If you have set up a deployment of OpenIDM in a custom directory, such as /path/to/openidm/production, you can modify the /etc/init.d/openidm script.
Open the openidm script in a text editor and navigate to the START_CMD line. At the end of the command, you should see the following line: org.forgerock.commons.launcher.Main -c bin/launcher.json >logs/server.out 2>&1 &' Include the path to the production directory.
In this case, you would add -p production as shown. Chapter 3. OpenIDM Command-Line Interface This chapter describes the basic command-line interface provided with OpenIDM. The command-line interface includes a number of utilities for managing an OpenIDM instance.
All of the utilities are subcommands of the cli.sh (UNIX) or cli.bat (Windows) scripts. To use the utilities, you can either run them as subcommands, or launch the cli script first, and then run the utility.
For example, to run the encrypt utility on a UNIX system: $ cd /path/to/openidm $./cli.sh Using boot properties at /path/to/openidm/conf/boot/boot.properties openidm# encrypt. Or $ cd /path/to/openidm $./cli.sh encrypt. By default, the command-line utilities run with the properties defined in your project's conf/boot/boot.properties file. If you run the cli.sh command by itself, it opens an OpenIDM-specific shell prompt: openidm# The startup and shutdown scripts are not discussed in this chapter.
For information about these scripts, see. The following sections describe the subcommands and their use. Examples assume that you are running the commands on a UNIX system. For Windows systems, use cli.bat instead of cli.sh. For a list of subcommands available from the openidm# prompt, run the cli.sh help command.
The help and exit options shown below are self-explanatory. The other subcommands are explained in the subsections that follow: local:keytool Export or import a SecretKeyEntry.
The Java Keytool does not allow for exporting or importing SecretKeyEntries. Local:encrypt Encrypt the input string. Local:secureHash Hash the input string.
Local:validate Validates all json configuration files in the configuration (default: /conf) folder. Basic:help Displays available commands. Basic:exit Exit from the console. Remote:update Update the system with the provided update file.
Remote:configureconnector Generate connector configuration. Remote:configexport Exports all configurations.
Remote:configimport Imports the configuration set from local file/directory. The following options are common to the configexport, configimport, and configureconnector subcommands. U or --user USER[:PASSWORD] Allows you to specify the server user and password. Specifying a username is mandatory.
If you do not specify a username, the following error is output to the OSGi console: Remote operation failed: Unauthorized. If you do not specify a password, you are prompted for one. This option is used by all three subcommands. --url URL The URL of the OpenIDM REST service. The default URL is This can be used to import configuration files from a remote running instance of OpenIDM.
This option is used by all three subcommands. -P or --port PORT The port number associated with the OpenIDM REST service. If specified, this option overrides any port number specified with the --url option. The default port is 8080.
This option is used by all three subcommands. 3.1. Using the configexport Subcommand The configexport subcommand exports all configuration objects to a specified location, enabling you to reuse a system configuration in another environment. For example, you can test a configuration in a development environment, then export it and import it into a production environment. This subcommand also enables you to inspect the active configuration of an OpenIDM instance. OpenIDM must be running when you execute this command. Usage is as follows: $./cli.sh configexport --user username:password export-location For example: $./cli.sh configexport --user openidm-admin:openidm-admin /tmp/conf On Windows systems, the export-location must be provided in quotation marks, for example.
3.2. Using the configimport Subcommand The configimport subcommand imports configuration objects from the specified directory, enabling you to reuse a system configuration from another environment. For example, you can test a configuration in a development environment, then export it and import it into a production environment. The command updates the existing configuration from the import-location over the OpenIDM REST interface. By default, if configuration objects are present in the import-location and not in the existing configuration, these objects are added. If configuration objects are present in the existing location but not in the import-location, these objects are left untouched in the existing configuration.
The subcommand takes the following options: -r, --replaceall, --replaceAll Replaces the entire list of configuration files with the files in the specified import location. Note that this option wipes out the existing configuration and replaces it with the configuration in the import-location. Objects in the existing configuration that are not present in the import-location are deleted. --retries (integer) New in OpenIDM 4.5.1-6, this option specifies the number of times the command should attempt to update the configuration if OpenIDM is not ready. Default value: 10 --retryDelay (integer) New in OpenIDM 4.5.1-6, this option specifies the delay (in milliseconds) between configuration update retries if OpenIDM is not ready. Default value: 500 Usage is as follows.
3.6. Using the keytool Subcommand The keytool subcommand exports or imports secret key values. The Java keytool command enables you to export and import public keys and certificates, but not secret or symmetric keys. The OpenIDM keytool subcommand provides this functionality.
Usage is as follows: $./cli.sh keytool [--export, --import] alias For example, to export the default OpenIDM symmetric key, run the following command: $./cli.sh keytool --export openidm-sym-default Using boot properties at /openidm/conf/boot/boot.properties Use KeyStore from: /openidm/security/keystore.jceks Please enter the password: [OK] Secret key entry with algorithm AES AES:606d80ae316be58e94439f91ad8ce1c0 The default keystore password is changeit. For security reasons, you must change this password in a production environment. For information about changing the keystore password, see. To import a new secret key named my-new-key, run the following command: $./cli.sh keytool --import my-new-key Using boot properties at /openidm/conf/boot/boot.properties Use KeyStore from: /openidm/security/keystore.jceks Please enter the password: Enter the key: AES:606d80ae316be58e94439f91ad8ce1c0 If a secret key of that name already exists, OpenIDM returns the following error: 'KeyStore contains a key with this alias'. 3.7. Using the validate Subcommand The validate subcommand validates all.json configuration files in your project's conf/ directory. Usage is as follows: $./cli.sh validate Executing./cli.sh Starting shell in /path/to/openidm Using boot properties at /path/to/openidm/conf/boot/boot.properties.........
[Validating] Load JSON configuration files from: [Validating] /path/to/openidm/conf [Validating] audit.json.... SUCCESS [Validating] authentication.json... [Validating] sync.json.....
SUCCESS [Validating] ui-configuration.json... SUCCESS [Validating] ui-countries.json.... SUCCESS [Validating] workflow.json.... Chapter 4. OpenIDM Web-Based User Interfaces OpenIDM provides a customizable, browser-based user interface. The functionality is subdivided into Administrative and Self-Service User Interfaces.
If you are administering OpenIDM, navigate to the Administrative User Interface, also known as the Admin UI. If OpenIDM is installed on the local system, you can get to the Admin UI at the following URL: In the Admin UI, you can configure connectors, customize managed objects, set up attribute mappings, manage accounts, and more. The Self-Service User Interface, also known as the Self-Service UI, provides role-based access to tasks based on BPMN2 workflows, and allows users to manage certain aspects of their own accounts, including configurable self-service registration. When OpenIDM starts, you can access the Self-Service UI at https://localhost:8443/. 4.1. Configuring OpenIDM from the Admin UI You can set up a basic configuration for OpenIDM with the Administrative User Interface (Admin UI). Through the Admin UI, you can connect to resources, configure attribute mapping and scheduled reconciliation, and set up and manage objects, such as users, groups, and devices. You can configure OpenIDM through Quick Start cards, and from the Configure and Manage drop-down menus.
Try them out, and see what happens when you select each option. In the following sections, you will examine the default Admin UI dashboard, and learn how to set up custom Admin UI dashboards. The Quick Start cards allow quick access to the labeled configuration options, described here: • Add Connector Use the Admin UI to connect to external resources. For more information, see. • Create Mapping Configure synchronization mappings to map objects between resources. For more information, see.
• Manage Role Set up managed provisioning or authorization roles. For more information, see. • Add Device Use the Admin UI to set up managed objects, including users, groups, roles, or even Internet of Things (IoT) devices. For more information, see. • Set Up Registration Configure User Self-Registration.
You can set up the OpenIDM Self-Service UI login screen, with a link that allows new users to start a verified account registration process. For more information, see. • Set Up Password Reset Configure user self-service Password Reset. You can configure OpenIDM to allow users to reset forgotten passwords. For more information, see.
• Manage User Allows management of users in the current internal OpenIDM repository. You may have to run a reconciliation from an external repository first. For more information, see. • Set Up System Configure how OpenIDM works, as it relates to.
4.2. Working With the Self-Service UI For all users, the Self-Service UI includes Dashboard and Profile links in the top menu bar. To access the Self-Service UI, start OpenIDM, then navigate to. If you have not installed a certificate that is trusted by a certificate authority, you are prompted with an Untrusted Connection warning the first time you log in to the UI.
The Dashboard includes a list tasks assigned to the user who has logged in, tasks assigned to the relevant group, processes available to be invoked, current notifications for that user, along with Quick Start cards for that user's profile and password. • User Registration: You can configure limited access that allows a current anonymous user to create their own accounts. To aid in this process, you can configure reCAPTCHA, email validation, and KBA questions.
• Forgotten Username: You can set up OpenIDM to allow users to recover forgotten usernames via their email addresses or first and last names. OpenIDM can then display that username on the screen, and / or email such information to that user. • Password Reset: You can set up OpenIDM to verify user identities via KBA questions. If email configuration is included, OpenIDM would email a link that allows users to reset their passwords. If you enable email functionality, the one solution that works for all three self-service functions is to configure an outgoing email service for OpenIDM, as described in.
You can configure user self-service through the UI and through configuration files. • In the UI, log into the Admin UI. You can enable these features when you click Configure >User Registration, Configure >Forgotten Username, and Configure >Password Reset.
• In the command-line interface, copy the following files from samples/misc to your working project-dir/conf directory: User Registration: selfservice-registration.json Forgotten username: selfservice-username.json Password reset: selfservice-reset.json Examine the ui-configuration.json file in the same directory. You can activate or deactivate User Registration and Password Reset by changing the value associated with the selfRegistration and passwordReset properties: { 'configuration': { 'selfRegistration': true, 'passwordReset': true, 'forgotUsername': true.
For each of these functions, you can configure several options, including. ReCAPTCHA Google reCAPTCHA helps prevent bots from registering users or resetting passwords on your system. For Google documentation, see. For directions on how to configure reCAPTCHA for user self-service, see. Email Validation / Email Username You can configure the email messages that OpenIDM sends to users, as a way to verify identities for user self-service. For more information, see.
If you configure email validation, you must also configure an outgoing email service in OpenIDM. To do so, click Configure >System Preferences >Email. For more information, read.
User Details You can modify the Identity Email Field associated with user registration; by default, it is set to mail. User Query When configuring password reset and forgotten username functionality, you can modify the fields that a user is allowed to query.
If you do, you may need to modify the HTML templates that appear to users who request such functionality. For more information, see. Valid Query Fields Property names that you can use to help users find their usernames or verify their identity, such as userName, mail, or givenName. Identity ID Field Property name associated with the User ID, typically _id. Identity Email Field Property name associated with the user email field, typically something like mail or email. Identity Service URL The path associated with the identity data store, such as managed/user.
KBA Stage You can modify the list of Knowledge-based Authentication (KBA) questions in the conf/selfservice.kba.json file. Users can then select the questions they will use to help them verify their own identities. For directions on how to configure KBA questions, see. For User Registration, you cannot configure these questions in the Admin UI. Password Reset Form You can change the Password Field for the Password Reset feature to specify a relevant password property such as password, pwd, or userPassword. Make sure the property you select matches the canonical form for user passwords. Snapshot Token OpenIDM User Self-Service uses JWT tokens, with a default token lifetime of 1800 seconds.
You can reorder how OpenIDM works with relevant self-service options, specifically reCAPTCHA, KBA stage questions, and email validation. Based on the following screen, users who need to reset their passwords will go through reCAPTCHA, followed by email validation, and then answer any configured KBA questions. 4.4. Customizing a UI Template You may want to customize information included in the Self-Service UI. These procedures do not address actual data store requirements. If you add text boxes in the UI, it is your responsibility to set up associated properties in your repositories. To do so, you should copy existing default template files in the openidm/ui/selfservice/default subdirectory to associated extension/ subdirectories. To simplify the process, you can copy some or all of the content from the openidm/ui/selfservice/default/templates to the openidm/ui/selfservice/extension/templates directory.
You can use a similar process to modify what is shown in the Admin UI. Status By default, accounts are shown as active.
To suspend an account, such as for a user who has taken a leave of absence, set that user's status to inactive. Manager You can assign a manager from the existing list of managed users.
Password As an administrator, you can create new passwords for users in the managed user repository. Provisioning Roles Used to specify how objects are provisioned to an external system. For more information, see. Authorization Roles Used to specify the authorization rights of a managed user within OpenIDM.
For more information, see. Direct Reports Users who are listed as managers of others have entries under the Direct Reports tab, as shown in the following illustration. Procedure 4.3. To Add a User Account • Log in to the Admin UI at • Click Manage >User. • Click New User. • Complete the fields on the New User page. Most of these fields are self-explanatory.
Be aware that the user interface is subject to policy validation, as described in. So, for example, the email address must be a valid email address, and the password must comply with the password validation settings that appear if you enter an invalid password. In a similar way, you can create accounts for other managed objects.
You can review new managed object settings in the managed.json file of your project-dir/conf directory. In the following procedures, you learn how to update, deactivate, and delete user accounts, as well as how to view that account in different user resources.
You can follow essentially the same procedures for other managed objects such as IoT devices. Procedure 4.6. To View an Account in External Resources The Admin UI displays the details of the account in the OpenIDM repository (managed/user). When a mapping has been configured between the repository and one or more external resources, you can view details of that account in any external system to which it is linked. As this view is read-only, you cannot update a user record in a linked system from within the Self-Service UI. By default, implicit synchronization is enabled for mappings from the managed/user repository to any external resource. This means that when you update a managed object, any mappings defined in the sync.json file that have the managed object as the source are automatically executed to update the target system.
You can see these changes in the Linked Systems section of a user's profile. To view a user's linked accounts: • Log in to the Admin UI at • Click Manage User >Username >Linked Systems. • The Linked Systems panel indicates the external mapped resource or resources. • Select the resource in which you want to view the account, from the Linked Resource list. The user record in the linked resource is displayed.
4.6. Configuring Account Relationships This section will help you set up relationships between human users and devices, such as IoT devices. You'll set this up with the help of the Admin UI schema editor, which allows you to create and customize managed objects such as Users and Devices as well as relationships between managed objects. You can also create these options in the managed.json file for your project. When complete, you will have users who can own multiple unique devices. If you try to assign the same device to more than one owner, OpenIDM will stop you with an error message. This section assumes that you have started OpenIDM with in the Samples Guide. After you have started OpenIDM with 'Sample 2b', go through the following procedures, where you will: • Set up a managed object named Device, with unique serial numbers for each device.
You can configure the searchable schema of your choice. See for details. • Set up a relationship from the Device to the User managed object. See for details. • Set up a reverse relationship from the User to the Device managed object. See for details. • Demonstrate the relationships.
Assign users to devices. See what happens when you try to assign a device to more than one user. For details, see. Procedure 4.7. Configuring Schema for a Device This procedure illustrates how you might set up a Device managed object, with schema that configures relationships to users. After you configure the schema for the Device managed object, you can collect information such as model, manufacturer, and serial number for each device. In the next procedure, you'll set up an owner schema property that includes a relationship to the User managed object.
• Click Configure >Managed Objects >New Managed Object. Give that object an appropriate IoT name. For this procedure, specify Device. You should also select a managed object icon.
• You should now see four tabs: Details, Schema, Scripts, and Properties. Click the Schema tab. • The items that you can add to the new managed object depend on the associated properties. The Schema tab includes the Readable Title of the device; in this case, set it to Device.
• You can add schema properties as needed in the UI. Click the Property button. Include the properties shown in the illustration: model, serialNumber, manufacturer, description, and category. • Initially, the new property is named Property 1. As soon as you enter a property name such as model, OpenIDM changes that property name accordingly. • To support UI-based searches of devices, make sure to set the Searchable option to true for all configured schema properties, unless it includes extensive text, In this case, you should set Searchable to false for the description property.
The Searchable option is used in the data grid for the given object. When you click Manage >Device (or another object such as User), OpenIDM displays searchable properties for that object. • After you save the properties for the new managed object type, OpenIDM saves those entries in the managed.json file in the project-dir/conf directory. • Now click Manage >Device >New Device. Add a device as shown in the following illustration. Procedure 4.8. Configure a Relationship from the Device Managed Object In this procedure, you will add a property to the schema of the Device managed object. • In the Admin UI, click Configure >Managed Objects >Device >Schema.
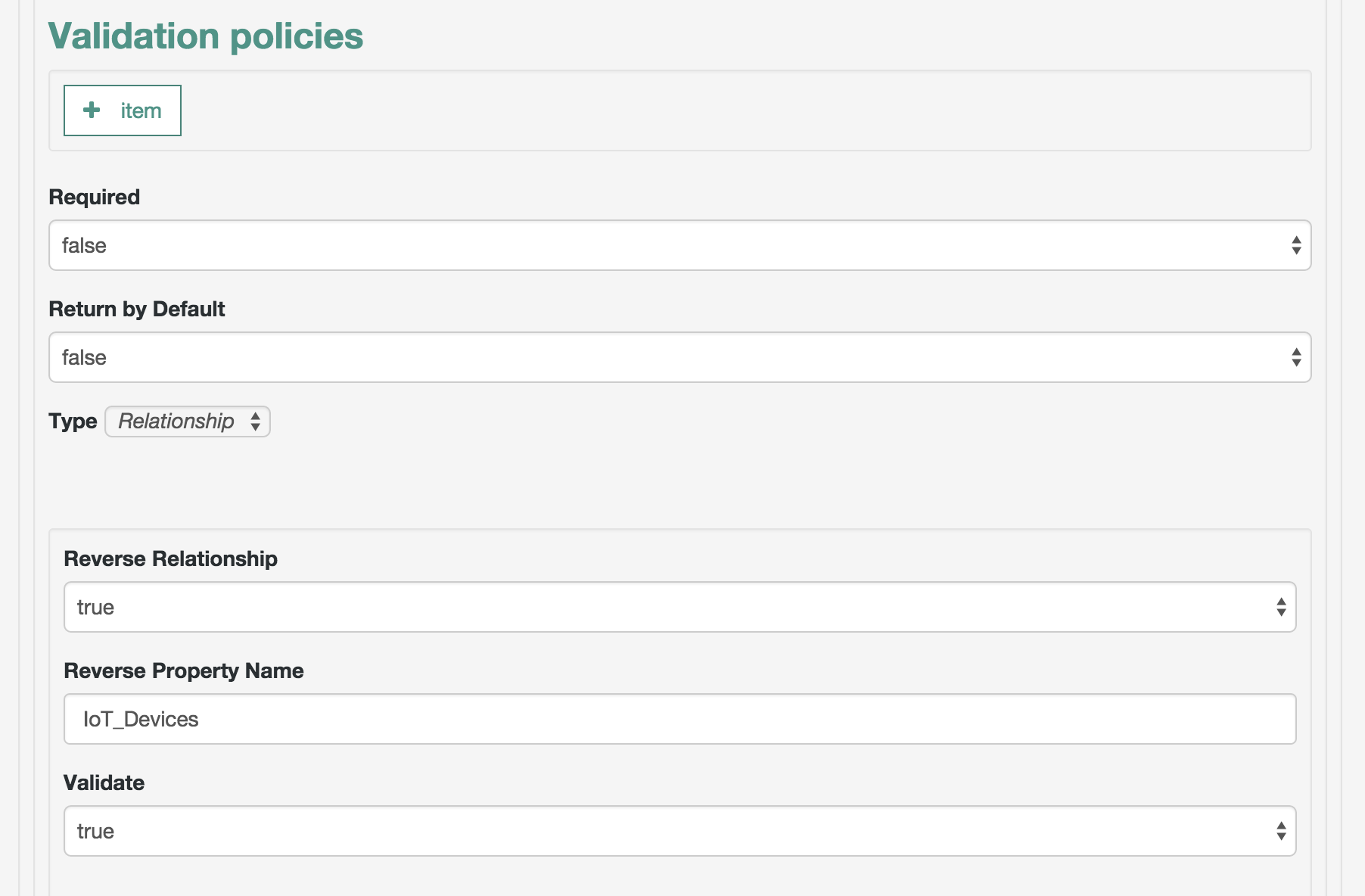
• Under the Schema tab, add a new property. For this procedure, we call it owner. Unlike other schema properties, set the Searchable property to false. • Scroll down to Validation Policies; click the Type box and select Relationship. This opens additional relationship options.
• Set up a Reverse Property Name of IoT_Devices. You'll use that reverse property name in the next. Procedure 4.9. Configure a Relationship From the User Managed Object In this procedure, you will configure an existing User Managed Object with schema to match what was created in. With the settings you create, OpenIDM supports a relationship between a single user and multiple devices. In addition, this procedure prevents multiple users from 'owning' any single device. • In the Admin UI, click Configure >Managed Objects >User >Schema. • Under the Schema tab, add a new property, called IoT_Devices.
• Make sure the searchable property is set to false, to minimize confusion in the relationship. Otherwise, you'll see every device owned by every user, when you click Manage >User. • For validation policies, you'll set up an array with a relationship.
Note how the reverse property name matches the property that you configured in. 4.9.1. OpenIDM UI Themes and Bootstrap You can configure a few features of the OpenIDM UI in the ui-themeconfig.json file in your project's conf/ subdirectory. However, to change most theme-related features of the UI, you must copy target files to the appropriate extension subdirectory, and then modify them as discussed in. The default configuration files for the Admin and Self-Service UIs are identical for theme configuration. By default the UI reads the stylesheets and images from the respective openidm/ui/ function/default directories.
Do not modify the files in this directory. Your changes may be overwritten the next time you update or even patch your system.
To customize your UI, first set up matching subdirectories for your system ( openidm/ui/admin/extension and openidm/ui/selfservice/extension). For example, assume you want to customize colors, logos, and so on. You can set up a new theme, primarily through custom Bootstrap CSS files, in appropriate extension/ subdirectories, such as openidm/ui/selfservice/extension/libs and openidm/ui/selfservice/extension/css. You may also need to update the 'stylesheets' listing in the ui-themeconfig.json file for your project, in the project-dir/conf directory. 'stylesheets': ['css/bootstrap-3.3.5-custom.css', 'css/structure.css', 'css/theme.css'].
You can find these stylesheets in the /css subdirectory. • bootstrap-3.3.5-custom.css: Includes custom settings that you can get from various Bootstrap configuration sites, such as the Bootstrap website. You may find the ForgeRock version of this in the config.json file in the ui/selfservice/default/css/common/structure/ directory. • structure.css: Supports configuration of structural elements of the UI. • theme.css: Includes customizable options for UI themes such as colors, buttons, and navigation bars.
If you want to set up custom versions of these files, copy them to the extension/css subdirectories. 4.10. Using an External System for Password Reset By default, the Password Reset mechanism is handled internally, in OpenIDM. You can reroute Password Reset in the event that a user has forgotten their password, by specifying an external URL to which Password Reset requests are sent. Note that this URL applies to the Password Reset link on the login page only, not to the security data change facility that is available after a user has logged in. To set an external URL to handle Password Reset, set the passwordResetLink parameter in the UI configuration file ( conf/ui-configuration.json) file. The following example sets the passwordResetLink to passwordResetLink: 'The passwordResetLink parameter takes either an empty string as a value (which indicates that no external link is used) or a full URL to the external system that handles Password Reset requests.
4.12. Changing the UI Path By default, the self service UI is registered at the root context and is accessible at the URL To specify a different URL, edit the project-dir/conf/ui.context-selfservice.json file, setting the urlContextRoot property to the new URL. For example, to change the URL of the self service UI to edit the file as follows: 'urlContextRoot': '/exampleui', Alternatively, to change the Self-Service UI URL in the Admin UI, follow these steps. Chapter 5. Managing the OpenIDM Repository OpenIDM stores managed objects, internal users, and configuration objects in a repository.
By default, OpenIDM uses OrientDB for its internal repository. In production, you must replace OrientDB with a supported JDBC repository, as described in in the Installation Guide. This chapter describes the JDBC repository configuration, the use of mappings in the repository, and how to configure a connection to the repository over SSL.
It also describes how to interact with the OpenIDM repository over the REST interface. • 'driverClass': string To use the JDBC driver manager to acquire a data source, set this property, as well as 'jdbcUrl', 'username', and 'password'. The driver class must be the fully qualified class name of the database driver to use for your database. Using the JDBC driver manager to acquire a data source is the most likely option, and the only one supported 'out of the box'. The remaining options in the sample repository configuration file assume that you are using a JDBC driver manager.
Example: 'driverClass': 'com.mysql.jdbc.Driver' • 'jndiName': string If you use JNDI to acquire the data source, set this property to the JNDI name of the data source. This option might be relevant if you want to run OpenIDM inside your own web container.
Example: 'jndiName': 'jdbc/my-datasource' • 'jtaName': string If you use an OSGi service to acquire the data source, set this property to a stringified version of the OsgiName. This option would only be relevant in a highly customized deployment, for example, if you wanted to develop your own connection pool. Example: 'jtaName': 'osgi:service/javax.sql.DataSource/(osgi.jndi.service.name=jdbc/openidm)' jdbcUrl The connection URL to the JDBC database. The URL should include all of the parameters required by your database.
For example, to specify the encoding in MySQL use 'characterEncoding=utf8'. Example: 'jdbcUrl': 'jdbc:mysql://localhost:3306/openidm?characterEncoding=utf8' databaseName The name of the database to which OpenIDM connects. Download Film The Sleeping Dictionary 2003 there. By default, this is openidm. Username The username with which to access the JDBC database.
Password The password with which to access the JDBC database. OpenIDM automatically encrypts clear string passwords.
To replace an existing encrypted value, replace the whole crypto-object value, including the brackets, with a string of the new password. ConnectionTimeout The period of time, in milliseconds, after which OpenIDM should consider an attempted connection to the database to have failed. The default period is 30000 milliseconds (30 seconds). ConnectionPool Database connection pooling configuration. Currently OpenIDM supports the BoneCP pool library only ( 'type': 'bonecp').
OpenIDM uses the default BoneCP configuration, except for the following parameters. You might need to adjust these parameters, according to your database workload. • partitionCount The partition count determines the lock segmentation in the connection pool. Each incoming connection request acquires a connection from a pool that has thread-affinity. Threads are dispatched to the appropriate lock by using a value of threadId% partitionCount.
A partition count that is greater than 1 protects the connection pool with more than a single lock, thereby reducing lock contention. By default, BoneCP creates a single partition. The JDBC Connection Configuration Files provided with OpenIDM set the partition count to 4. • maxConnectionsPerPartition The maximum number of connections to create per partition. The maximum number of database connections is equal to partitionCount * maxConnectionsPerPartition. BoneCP does not create all these connections at once, but starts off with the minConnectionsPerPartition and gradually increases connections as required. By default, BoneCP creates a maximum of 20 connections per partition.
The JDBC Connection Configuration Files provided with OpenIDM set the maximum connections per partition to 25. • minConnectionsPerPartition The number of connections to start off with, per partition. The minimum number of database connections is equal to partitionCount * minConnectionsPerPartition. By default, BoneCP starts with a minimum of 1 connection per partition. The JDBC Connection Configuration Files provided with OpenIDM set the minimum connections per partition to 5. For more information about the BoneCP configuration parameters, see.
5.2.1. Using Generic Mappings Generic mapping speeds up development, and can make system maintenance more flexible by providing a more stable database structure. However, generic mapping can have a performance impact and does not take full advantage of the database facilities (such as validation within the database and flexible indexing). In addition, queries can be more difficult to set up. In a generic table, the entire object content is stored in a single large-character field named fullobject in the mainTable for the object. To search on specific fields, you can read them by referring to them in the corresponding properties table for that object.
The disadvantage of generic objects is that, because every property you might like to filter by is stored in a separate table, you must join to that table each time you need to filter by anything. The following diagram shows a pared down database structure for the default generic table, and indicates the relationship between the main table and the corresponding properties table for each object. MainTable (string, mandatory) Indicates the main table in which data is stored for this resource.
The complete object is stored in the fullobject column of this table. The table includes an entityType foreign key that is used to distinguish the different objects stored within the table. In addition, the revision of each stored object is tracked, in the rev column of the table, enabling multi version concurrency control (MVCC).
For more information, see. PropertiesTable (string, mandatory) Indicates the properties table, used for searches. The contents of the properties table is a defined subset of the properties, copied from the character large object (CLOB) that is stored in the fullobject column of the main table. The properties are stored in a one-to-many style separate table. The set of properties stored here is determined by the properties that are defined as searchable.
The stored set of searchable properties makes these values available as discrete rows that can be accessed with SQL queries, specifically, with WHERE clauses. It is not otherwise possible to query specific properties of the full object. Support for data types in columns is restricted to String ( VARCHAR in the case of MySQL).
If you use a different data type, such as DATE or TIMESTAMP, your database must attempt to convert from String to the other data type. This conversion is not guaranteed to work. If the conversion does work, the format might not be the same when it is read from the database as it was when it was saved. For example, your database might parse a date in the format and return the date in the format 2012-12-12 when the property is read. 5.3. Configuring SSL with a JDBC Repository To configure SSL with a JDBC repository, you need to import the CA certificate file for the server into the OpenIDM truststore. That certificate file could have a name like ca-cert.pem.
If you have a different genuine or self-signed certificate file, substitute accordingly. To import the CA certificate file into the OpenIDM truststore, use the keytool command native to the Java environment, typically located in the /path/to/jre-version/bin directory. On some UNIX-based systems, /usr/bin/keytool may link to that command. 5.4.1. Changing the Repository Password In the case of an embedded OrientDB repository, the default username and password are admin and admin. You can change the default password, by sending the following POST request on the repo endpoint: $ curl --cacert self-signed.crt --header 'X-OpenIDM-Username: openidm-admin' --header 'X-OpenIDM-Password: openidm-admin' --request POST 'You must restart OpenIDM for the change to take effect. Chapter 6. Configuring OpenIDM OpenIDM configuration is split between.properties and container configuration files, and also dynamic configuration objects. Most of OpenIDM's configuration files are stored in your project's conf/ directory, as described in.
OpenIDM stores configuration objects in its internal repository. You can manage the configuration by using REST access to the configuration objects, or by using the JSON file-based views. Several aspects of the configuration can also be managed by using the Admin UI, as described in. The following list describes the single instance configuration objects: • The audit configuration specifies how audit events are logged. • The authentication configuration controls REST access. • The cluster configuration defines how one OpenIDM instance can be configured in a cluster. • The endpoint configuration controls any custom REST endpoints.
• The info configuration points to script files for the customizable information service. • The managed configuration defines managed objects and their schemas. • The policy configuration defines the policy validation service. • The process access configuration defines access to configured workflows. Repo-type configuration such as repo.orientdb or repo.jdbc configures the internal repository. • The router configuration specifies filters to apply for specific operations.
• The script configuration defines the parameters that are used when compiling, debugging, and running JavaScript and Groovy scripts. • The sync configuration defines the mappings that OpenIDM uses when it synchronizes and reconciles managed objects. • The ui configuration defines the configurable aspects of the default user interfaces. • The workflow configuration defines the configuration of the workflow engine.
OpenIDM stores managed objects in the repository, and exposes them under /openidm/managed. System objects on external resources are exposed under /openidm/system. The following image shows the paths to objects in the OpenIDM namespace. When you change OpenIDM's configuration objects, take the following points into account: • OpenIDM's authoritative configuration source is the internal repository. JSON files provide a view of the configuration objects, but do not represent the authoritative source.
OpenIDM updates JSON files after making configuration changes, whether those changes are made through REST access to configuration objects, or through edits to the JSON files. • OpenIDM recognizes changes to JSON files when it is running. OpenIDM must be running when you delete configuration objects, even if you do so by editing the JSON files. • Avoid editing configuration objects directly in the internal repository. Rather, edit the configuration over the REST API, or in the configuration JSON files to ensure consistent behavior and that operations are logged. • OpenIDM stores its configuration in the internal database by default.
If you remove an OpenIDM instance and do not specifically drop the repository, the configuration remains in effect for a new OpenIDM instance that uses that repository. For testing or evaluation purposes, you can disable this persistent configuration in the conf/system.properties file by uncommenting the following line: # openidm.config.repo.enabled=false Disabling persistent configuration means that OpenIDM will store its configuration in memory only.
You should not disable persistent configuration in a production environment. 6.3.2. Disabling Automatic Configuration Updates By default, OpenIDM polls the JSON files in the conf directory periodically for any changes to the configuration. In a production system, it is recommended that you disable automatic polling for updates to prevent untested configuration changes from disrupting your identity service. To disable automatic polling for configuration changes, edit the conf/system.properties file for your project, and uncomment the following line: # openidm.fileinstall.enabled=false This setting also disables the file-based configuration view, which means that OpenIDM reads its configuration only from the repository.
Before you disable automatic polling, you must have started the OpenIDM instance at least once to ensure that the configuration has been loaded into the repository. Be aware, if automatic polling is enabled, OpenIDM immediately uses changes to scripts called from a JSON configuration file. When your configuration is complete, you can disable writes to configuration files.
To do so, add the following line to the conf/config.properties file for your project: felix.fileinstall.enableConfigSave=false. JVM Property Example Values Description -Dhttps.proxyHost proxy.example.com, 192.168.0.1 Hostname or IP address of the proxy server -Dhttps.proxyPort 8443, 9443 Port number used by OpenIDM If an insecure port is acceptable, you can also use the -Dhttp.proxyHost and -Dhttp.proxyPort options. You can add these JVM proxy properties to the value of OPENIDM_OPTS in your startup script ( startup.sh or startup.bat): # Only set OPENIDM_OPTS if not already set [ -z '$OPENIDM_OPTS' ] && OPENIDM_OPTS='-Xmx1024m -Xms1024m -Dhttps.proxyHost=localhost -Dhttps.proxyPort=8443'.
Note the following limitations when you use property value substitution: • You cannot reference complex objects or properties with syntaxes other than string. Property values are resolved from the boot.properties file or from the system properties and the value of these properties is always in string format. Property substitution of boolean values is currently only supported in stringified format, that is, resulting in 'true' or 'false'. • Substitution of encrypted property values is not supported.
• javascript.recompile.minimumInterval - minimum time after which a script can be recompiled. The default value is 60000, or 60 seconds. This means that any changes made to scripts will not get picked up for up to 60 seconds. If you are developing scripts, reduce this parameter to around 100 (100 milliseconds). Groovy Specifies compilation and debugging options related to Groovy scripts. Many of these options are commented out in the default script configuration file. Remove the comments to set these properties.
• groovy.warnings - the log level for Groovy scripts. Possible values are none, likely, possible, and paranoia.
• groovy.source.encoding - the encoding format for Groovy scripts. Possible values are UTF-8 and US-ASCII. • groovy.target.directory - the directory to which compiled Groovy classes will be output. The default directory is install-dir/classes. • groovy.target.bytecode - the bytecode version that is used to compile Groovy scripts. The default version is 1.5.
• groovy.classpath - the directory in which the compiler should look for compiled classes. The default classpath is install-dir/lib. To call an external library from a Groovy script, you must specify the complete path to the.jar file or files, as a value of this property. 7.1. Accessing Data Objects By Using Scripts OpenIDM's uniform programming model means that all objects are queried and manipulated in the same way, using the Resource API.
The URL or URI that is used to identify the target object for an operation depends on the object type. For an explanation of object types, see. For more information about scripts and the objects available to scripts, see. You can use the Resource API to obtain managed, system, configuration, and repository objects, as follows: val = openidm.read('managed/organization/mysampleorg') val = openidm.read('system/mysystem/account') val = openidm.read('config/custom/mylookuptable') val = openidm.read('repo/custom/mylookuptable') For information about constructing an object ID, see.
You can update entire objects with the update() function, as follows: openidm.update('managed/organization/mysampleorg', object) openidm.update('system/mysystem/account', object) openidm.update('config/custom/mylookuptable', object) openidm.update('repo/custom/mylookuptable', object) You can apply a partial update to a managed or system object by using the patch() function: openidm.patch('managed/organization/mysampleorg', rev, value) The create(), delete(), and query() functions work the same way. 7.3.3. Native Query Expressions Native query expressions are supported for all managed objects and system objects, and can be called directly, rather than being defined in the repository configuration. Native queries are intended specifically for internal callers, such as custom scripts, and should be used only in situations where the common filter or parameterized query facilities are insufficient.
For example, native queries are useful if the query needs to be generated dynamically. The query expression is specific to the target resource. For repositories, queries use the native language of the underlying data store.
For system objects that are backed by OpenICF connectors, queries use the applicable query language of the system resource. Native queries on the repository are made using the _queryExpression keyword. For example: $ curl --cacert self-signed.crt --header 'X-OpenIDM-Username: openidm-admin' --header 'X-OpenIDM-Password: openidm-admin' 'Unless you have specifically enabled native queries over REST, the previous command returns a 403 access denied error message. Native queries are not portable and do not guard against injection attacks.
Such query expressions should therefore not be used or made accessible over the REST interface or over HTTP in production environments. They should be used only via the internal Resource API. If you want to enable native queries over REST for development, see. Alternatively, if you really need to expose native queries over HTTP, in a selective manner, you can design a custom endpoint to wrap such access. The following paging parameters are supported: _pagedResultsCookie Opaque cookie used by the server to keep track of the position in the search results. The format of the cookie is a string value.
The server provides the cookie value on the first request. You should then supply the cookie value in subsequent requests until the server returns a null cookie, meaning that the final page of results has been returned. Paged results are enabled only if the _pageSize is a non-zero integer. _pagedResultsOffset Specifies the index within the result set of the number of records to be skipped before the first result is returned. The format of the _pagedResultsOffset is an integer value. When the value of _pagedResultsOffset is greater than or equal to 1, the server returns pages, starting after the specified index. This request assumes that the _pageSize is set, and not equal to zero.
For example, if the result set includes 10 records, the _pageSize is 2, and the _pagedResultsOffset is 6, the server skips the first 6 records, then returns 2 records, 7 and 8. The _pagedResultsCookie value would then be 8 (the index of the last returned record) and the _remainingPagedResults value would be 2, the last two records (9 and 10) that have not yet been returned. If the offset points to a page beyond the last of the search results, the result set returned is empty. Note that the totalPagedResults and _remainingPagedResults parameters are not supported for all queries.
Where they are not supported, their returned value is always -1. _pageSize An optional parameter indicating that query results should be returned in pages of the specified size. For all paged result requests other than the initial request, a cookie should be provided with the query request.
The default behavior is not to return paged query results. If set, this parameter should be an integer value, greater than zero. Chapter 8. Managing Users, Groups, Roles and Relationships OpenIDM provides a default schema for typical managed object types, such as users and roles, but does not control the structure of objects that you store in the OpenIDM repository. You can modify or extend the schema for the default object types, and you can set up a new managed object type for any item that can be collected in a data set. For example, with the right schema, you can set up any device associated with the Internet of Things (IoT). Managed objects and their properties are defined in your project's conf/managed.json file.
Note that the schema defined in this file is not a comprehensive list of all the properties that can be stored in the managed object repository. If you use a generic object mapping, you can create a managed object with any arbitrary property, and that property will be stored in the repository. For more information about explicit and generic object mappings, see. This chapter describes how to work with the default managed object types and how to create new object types as required by your deployment.
For more information about the OpenIDM object model, see. • name - the name of the property • title - the name of the property, in human-readable language, used to display the property in the UI • description - a description of the property • viewable - specifies whether this property is viewable in the object's profile in the UI). Boolean, true or false ( true by default).
• searchable - specifies whether this property can be searched in the UI. A searchable property is visible within the Managed Object data grid in the Self-Service UI. Note that for a property to be searchable in the UI, it must be indexed in the repository configuration. For information on indexing properties in a repository, see.
Boolean, true or false ( false by default). • userEditable - specifies whether users can edit the property value in the UI. This property applies in the context of the self-service UI, where users are able to edit certain properties of their own accounts. Boolean, true or false ( false by default). • minLength - the minimum number of characters that the value of this property must have. • pattern - any specific pattern to which the value of the property must adhere.
For example, a property whose value is a date might require a specific date format. • policies - any policy validation that must be applied to the property.
For more information on managed object policies, see. • required - specifies whether the property must be supplied when an object of this type is created. Boolean, true or false. • type - the data type for the property value; can be String, Array, Boolean, Integer, Number, Object, or Resource Collection. • isVirtual - specifies whether the property takes a static value, or whether its value is calculated 'on the fly' as the result of a script.
Boolean, true or false. • returnByDefault - for non-core attributes (virtual attributes and relationship fields), specifies whether the property will be returned in the results of a query on an object of this type if it is not explicitly requested. Virtual attributes and relationship fields are not returned by default.
When configured in an array within a relationship, always set to false Boolean, true or false. The _ref property points to the ID of the managed role that has been granted to the user. This particular example uses a client-assigned ID that is the same as the role name, to make the example easier to understand. All other examples in this chapter use system-assigned IDs.
In production, you should use system-assigned IDs for role objects. The following sections describe how to create, read, update, and delete managed roles, and how to grant roles to users. For information about how roles are used to provision users to external systems, see. For a sample that demonstrates the basic CRUD operations on roles, see in the Samples Guide. 8.4.3.2.1. Granting Roles Based on a Condition A role that is granted based on a defined condition is called a conditional role. To create a conditional role, include a query filter in the role definition. To create a conditional role by using the Admin UI, select Condition on the role Details page, then define the query filter that will be used to assess the condition.
In the following example, the role fr-employee will be granted only to those users who live in France (whose country property is set to FR). 8.4.4. Using Temporal Constraints to Restrict Effective Roles To restrict the period during which a role is effective, you can set a temporal constraint on the role itself, or on the role grant. A temporal constraint that is set on a role definition applies to all grants of that role. A temporal constraint that is set on a role grant enables you to specify the period that the role is valid per user. For example, you might want a role definition such as contractors-2016 to apply to all contract employees only for the year 2016. Or you might want a contractors role to apply to an individual user only during the duration of his contract of employment.
The following sections describe how to set temporal constraints on role definitions, and on individual role grants. 8.4.4.1. Adding a Temporal Constraint to a Role Definition When you create a role, you can include a temporal constraint in the role definition, which restricts the validity of the entire role, regardless of how that role is granted.
Temporal constraints are expressed as a duration in ISO 8601 date and time format. For more information on this format, see. To restrict the period during which a role is valid by using the Admin UI, select Temporal Constraint on the role Details page, then select the timezone and start and end dates for the required period. In the following example, the role contractor is effective from January 1st, 2016 to January 1st, 2017. 8.4.5. Querying a User's Manual and Conditional Roles The easiest way to check what roles have been granted to a user, either manually, or as the result of a condition, is to look at the user's entry in the Admin UI.
Select Manage >User, click on the user whose roles you want to see, and select the Provisioning Roles tab. To obtain a similar list over the REST interface, you can query the user's roles property. The following sample query shows that scarter has been granted two roles - an employee role (with ID 6bf4701a-7579-43c4-8bb4-7fd6cac552a1) and an fr-employee role (with ID 00561df0-1e7d-4c8a-9c1e-3b). 8.4.8. Working With Role Assignments Authorization roles control access to OpenIDM itself. Provisioning roles define rules for how attribute values are updated on external systems. These rules are configured through assignments that are attached to a provisioning role definition. The purpose of an assignment is to provision an attribute or set of attributes, based on an object's role membership.
The synchronization mapping configuration between two resources (defined in the sync.json file) provides the basic account provisioning logic (how an account is mapped from a source to a target system). Role assignments provide additional provisioning logic that is not covered in the basic mapping configuration. The attributes and values that are updated by using assignments might include group membership, access to specific external resources, and so on.
A group of assignments can collectively represent a role. Assignment objects are created, updated and deleted like any other managed object, and are attached to a role by using the relationships mechanism, in much the same way as a role is granted to a user. Assignment are stored in the repository and are accessible at the context path /openidm/managed/assignment. This section.